Seismic Internet-linked tracking systems are vulnerable to cyber attacks that could interrupt data collection and transmission, warn researchers who have checked the devices for weak points. Popular security problems such as unencrypted files, unsafe protocols, and weak user authentication mechanisms are among the biggest culprits who leave seismological networks exposed to security breaches, Michael Samios of the Athens National Observatory and colleagues write in a new study published in the Seismological Research Letters.
A new study by Michael Samios of the National Observatory of Athens and his colleagues highlights the cybersecurity vulnerabilities of internet-connected seismic equipment, used to detect and record earthquakes.
Regular security problems associated with such equipment involve unencrypted files, unencrypted protocols, and insufficient user authentication mechanisms. These problems make seismological networks vulnerable to security breaches. Modern seismic stations are now implemented as an Internet-of-Things (IoT) station, with physical devices that connect and exchange data with other devices and systems over the Internet. Samios and his colleagues identified vulnerabilities to equipment typically used in IoT systems by IT security experts in their test attacks on various brands of seismographs, accelerographs, and GPS receivers.
Researchers tested attacks on multiple brands of seismographs, accelerographs, and (Global Navigation Satellite System) receivers. Samios and his colleagues have demonstrated the introduction of Denial-of-Service (DoS) attacks against computers. The DoS attacks led to the unavailability of the computers and allowed the extraction of usernames and passwords.
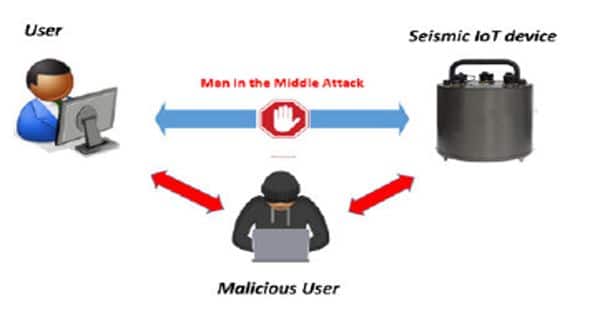
“It seems that most seismologists and network operators are unaware of the vulnerabilities of their IoT devices, and the potential risk that their monitoring networks are exposed to,” said Samios. “Educating and supporting seismologists on information security is imperative, as in most cases unauthorized users will try to gain access through a legitimate user’s computer to abuse monitoring networks and IoT devices.”
By leveraging these vulnerabilities, a malicious user may change geophysical data, delay data transmission and delivery, or trigger false alarms in earthquake early warning systems, the researchers observed, leading the public to lose interest in seismic detection and possibly influencing emergency and economic response to a seismic event.
Samios and associates also launched a safety review of the seismic and GSP systems connected to their own monitoring networks following a security incident at one of their seismic stations. There are many possible vulnerabilities in the protection of these systems, they noted, including physical security at often distant sites, difficulties and costs in upgrading hardware and software security, the use of non-encrypted protocols, and default or simply login.
Using their cryptography expertise, researchers tested these weak points using a traditional “ethical hacking” method to track, scan and obtain access to geophysical devices with their default settings. The most prominent security concerns found included a lack of data protection, poor user authentication protocols, and a lack of stable initial default setup.
Samios and colleagues were able to demonstrate a successful Denial-of-Service or DOS attack on the computers, leaving them inaccessible for the attack time, as well as retrieving usernames and passwords for some of the devices.
“Security weaknesses between different devices do not depend on the type of the device, but whether this device uses insecure protocols, outdated software, and a potentially insecure default configuration,” Samios said. “It is interesting, though, that while these vulnerabilities normally appear on low-cost IoT devices priced at $50 or less, it was also confirmed that they are observed even in seismological and GNSS devices that cost many times more.”
As part of their experiments, the study team was also able to intercept the seismological data transmitted via the SeedLink protocol, a data transmission facility used by many seismologists. SeedLink may lack some of the encryption and authentication protocols required to keep data secure, Samios said. He noticed that the researchers were able to modify waveforms transferred via SeedLink in a follow-up lab experiment not included in the SRL article.
“This could potentially generate or conceal alarms on earthquake early warning and seismic monitoring systems, leading to disturbing situations,” he said. Although computer vendors and data transmission providers should take action to enhance security features such as data encryption, Samios said, seismic network operators should collaborate with information security consultants to help them build better consumer processes and improve hardware and software systems.