Quantum key distribution has long held the promise of communication security that conventional cryptography cannot provide. An international team of scientists has now experimentally demonstrated, for the first time, a method of quantum key distribution based on high-quality quantum entanglement, which provides much broader security guarantees than previous schemes.
The art of cryptography is to transform messages so that they are meaningless to everyone except the intended recipients. Modern cryptographic schemes, such as those that underpin digital commerce, prevent adversaries from illegitimately deciphering messages – such as credit-card information – by requiring them to perform mathematical operations that consume an inordinate amount of computational power. However, beginning in the 1980s, ingenious theoretical concepts were introduced in which security is not dependent on the eavesdropper’s finite number-crunching capabilities.
Instead, fundamental quantum physics laws limit how much information, if any, an adversary can eventually intercept. Security can be guaranteed in one such concept with only a few general assumptions about the physical apparatus used. Implementations of such “device-independent” schemes have long been desired but have remained elusive. That is, until now. An international team of researchers from the University of Oxford, EPFL, ETH Zurich, the University of Geneva, and CEA report the first demonstration of this type of protocol in Nature, paving the way for practical devices with such high security.
Once the legitimate parties have ensured for a given round of communication that they, and only they, share such a key, pretty much all the other communication can happen in plain view, for everyone to see. The question, then, is how to ensure that only the legitimate parties share a secret key. The process of accomplishing this is known as ‘key distribution’.
The key is a secret
It is all about keeping information private in secure communication. As a result, it may come as a surprise that in real-world applications, many transactions between legitimate users take place in public. The key point is that the sender and receiver do not have to keep their entire communication hidden. In essence, they only need to share one ‘secret’; in practice, this secret is a string of bits known as a cryptographic key, which allows anyone in possession of it to convert coded messages into meaningful information.
Once the legitimate parties have ensured for a given round of communication that they, and only they, share such a key, pretty much all the other communication can happen in plain view, for everyone to see. The question, then, is how to ensure that only the legitimate parties share a secret key. The process of accomplishing this is known as ‘key distribution’.
In the cryptographic algorithms underlying, for instance, RSA — one of the most widely used cryptographic systems – key distribution is based on the (unproven) conjecture that certain mathematical functions are easy to compute but hard to revert. More specifically, RSA relies on the fact that for today’s computers it is hard to find the prime factors of a large number, whereas it is easy for them to multiply known prime factors to obtain that number.
Mathematical difficulty ensures secrecy. But what seems impossible today might be simple tomorrow. Famously, quantum computers can find prime factors significantly faster than classical computers. Once quantum computers with a large enough number of qubits become available, RSA encoding will be broken.
However, quantum theory provides the foundation not only for cracking the cryptosystems at the heart of digital commerce, but also for a potential solution: a method entirely different from RSA for distributing cryptographic keys – one that has nothing to do with the difficulty of performing mathematical operations, but with fundamental physical laws. Enter quantum key distribution, or QKD for short.

Quantum-certified security
In 1991, the Polish-British physicist Artur Ekert showed in a seminal paper that the security of the key-distribution process can be guaranteed by directly exploiting a property that is unique to quantum systems, with no equivalent in classical physics: quantum entanglement. Quantum entanglement refers to certain types of correlations in the outcomes of measurements performed on separate quantum systems. Importantly, quantum entanglement between two systems is exclusive, in that nothing else can be correlated to these systems.
In the context of cryptography, this means that the sender and receiver can produce shared outcomes through entangled quantum systems without a third party gaining secret knowledge of these outcomes. Eavesdropping leaves traces that clearly identify the intruder. In short, the legitimate parties can interact with one another in ways that are fundamentally beyond the control of any adversary, thanks to quantum theory. An equivalent security guarantee is provably impossible in classical cryptography.
Over time, it was discovered that QKD schemes based on Ekert’s ideas can have an additional remarkable benefit: users only need to make very general assumptions about the devices used in the process. Earlier forms of QKD based on other basic principles, on the other hand, necessitate detailed knowledge of the inner workings of the devices used. The novel type of QKD is now known as ‘device-independent QKD’ (DIQKD), and its experimental implementation has become a major goal in the field. As a result, the excitement is understandable, as such a groundbreaking experiment has now been completed.
Culmination of years of work
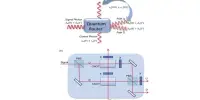
The scale of the challenge is reflected in the breadth of the team, which combines leading experts in theory and experiment. The experiment involved two single ions – one for the sender and one for the receiver — confined in separate traps that were connected with an optical-fiber link. In this basic quantum network, entanglement between the ions was generated with record-high fidelity over millions of runs.
The protocol could not have been run in a practically meaningful manner without such a consistent source of high-quality entanglement. Equally important was demonstrating that the entanglement is being properly exploited, which is accomplished by demonstrating that conditions known as Bell inequalities are violated. Furthermore, significant advances, in theory, were required for data analysis and efficient extraction of the cryptographic key.
The ‘legitimate parties’ — the ions — were all housed in the same laboratory during the experiment. However, there is a clear path to increasing the distance between them to kilometers and beyond. With that perspective, together with further recent progress made in related experiments in Germany and China, there is now a real prospect of turning the theoretical concept of Ekert into practical technology.