According to researchers who have examined the devices for flaws, seismic monitoring devices connected to the internet are vulnerable to cyberattacks that could disrupt data collection and processing.
Non-encrypted data, insecure protocols, and poor user authentication mechanisms are among the most common security issues that leave seismological networks vulnerable to security breaches, according to Michael Samios of the National Observatory of Athens and colleagues in a new study published in Seismological Research Letters.
Modern seismic stations are now built as Internet-of-Things (IoT) stations, with physical devices that connect to and exchange data with other devices and systems via the Internet. Samios and his colleagues identified threats to the equipment that information technology security professionals commonly find in IoT devices in their test attacks on different brands of seismographs, accelerographs, and GNSS receivers.
Seismic monitoring devices linked to the internet are vulnerable to cyberattacks that could disrupt data collection and processing, say researchers who have probed the devices for weak points.
“It appears that most seismologists and network operators are unaware of the vulnerabilities of their IoT devices, as well as the potential risk to their monitoring networks,” Samios said. “Educating and assisting seismologists on information security is critical, as unauthorized users will frequently attempt to gain access through a legitimate user’s computer in order to abuse monitoring networks and IoT devices.”
A malicious user could alter geophysical data, slow down data transmission and processing, or generate false alarms in earthquake early warning systems by exploiting these vulnerabilities, according to the researchers, causing the public to lose trust in seismic monitoring and potentially affecting emergency and economic responses to a seismic event.
Following a security incident at one of their seismic stations, Samios and colleagues conducted a security assessment of seismic and GNSS devices connected to their own monitoring networks. They identified several potential security flaws in these devices, including physical security in sometimes remote locations, the difficulties and costs of updating hardware and software security, the use of non-encrypted protocols, and default or easy login credentials.
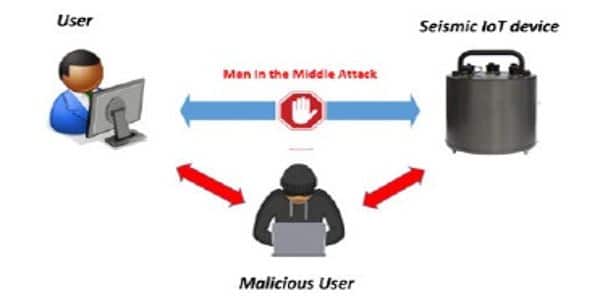
The researchers used their cybersecurity skills to test these flaws by surveilling, scanning, and gaining access to geophysical devices with their default settings. They discovered the most significant security issues to be a lack of data encryption, weak user authentication protocols, and the absence of a secure initial-default configuration.
Samios and colleagues were able to demonstrate the successful launch of a denial-of-service (DOS) attack against the devices, rendering them inoperable for the duration of the attack, as well as retrieve usernames and passwords for some of the devices.
“Security flaws between different devices are determined not by the type of device, but by whether this device uses insecure protocols, outdated software, and a potentially insecure default configuration,” Samios explained. “It is worth noting, however, that while these vulnerabilities are typically found in low-cost IoT devices priced at $50 or less, it has also been confirmed that they are found in seismological and GNSS devices that cost many times as much.”
The research team was also able to intercept seismological data transmitted via the SeedLink protocol, a data transmission service used by many seismologists, as part of their tests. According to Samios, SeedLink may lack some of the necessary encryption and authentication protocols to keep data secure. He mentioned that the researchers were able to manipulate waveforms transferred by SeedLink in a follow-up lab experiment that was not included in the SRL paper.
“This could potentially generate or conceal alarms on earthquake early warning and seismic monitoring systems, resulting in troubling situations,” he said.
While device manufacturers and data transmission services should improve security functions such as data encryption, seismic network operators can collaborate with information security experts to develop safer user practices and improve hardware and software systems, according to Samios.